World is implementing Personal Custody, an evolution in data custody recommended by privacy experts, that was first announced with the introduction of World ID 2.0.
What is Personal Custody, and how does it benefit you?
Personal data custody, or Personal Custody, means that the information (images, metadata and derived data) generated at the Orb and used to generate the iris code during World ID verification is held on your device. This approach gives you control over the flow of this data—not just deletion, but any future use prior to being deleted. Previously, this information was deleted by default.
In addition to giving you control, Personal Custody unlocks new World ID use cases by enabling Face Authentication for high security applications. With Face Authentication, you can verify at any time that you are the same person that received your World ID when verifying at an Orb. Importantly, this works locally on your device, without your data leaving your phone.
For World, giving you control over your data flow with Personal Custody is a significant step towards solidifying the project’s user-centric architecture and building an even more robust and secure World ID network.
How does Personal Custody work?
At a high level, Personal Custody involves four components: your device, the Orb, a data package containing your images and a temporary backend storage for transit. Importantly, the backend cannot decrypt your data package.
Here’s how the process works:
- Your phone generates a public-private key pair to encrypt your data, then transfers the public key to the backend.
- The backend generates additional keys for all data that requires double encryption and passes the public keys to the Orb.
- During verification, the Orb creates the necessary images to verify your World ID.
- The Orb then creates your individual data packages, encrypts them, signs them to ensure authenticity and security, then sends them to the backend before deleting the images.
- Your encrypted data packages are downloaded to your phone prior to their deletion from the backend.
Since all data is encrypted by your public key, the end result of this process is a collection of encrypted data packages that reside exclusively on your device. Your information is always deleted from the Orb once it has been sent to your device, and the use of double encryption within the end-to-end encryption envelope is a safeguard to protect the confidentiality and privacy of your data in the event your device is compromised.
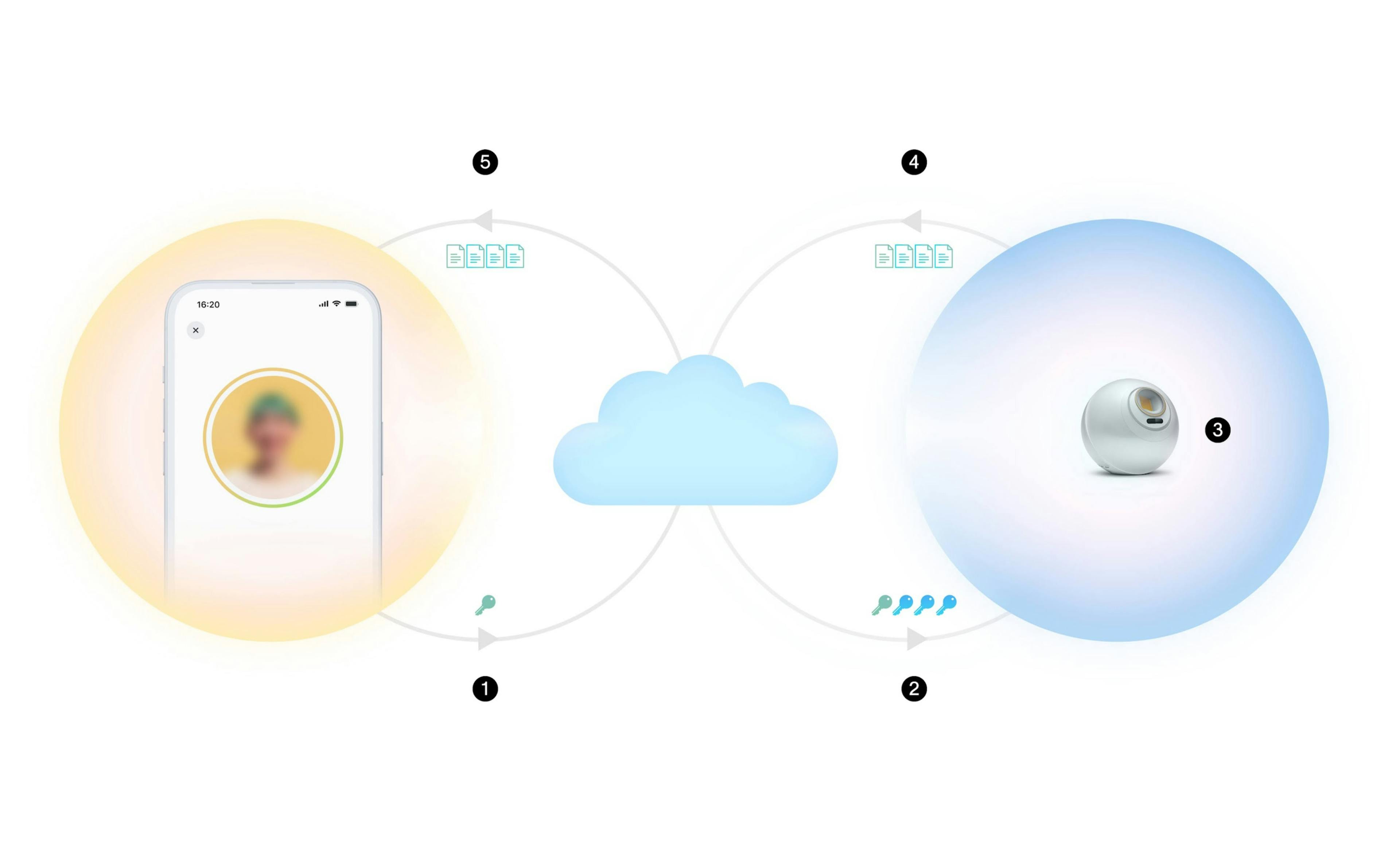
The illustration above is designed to help visualize the flow of keys and data throughout this process. User encrypted files are biometric templates that are necessary for performing Face Authentication and for enrolling in the system, while double encrypted files are images that are not yet used but will be relevant for future system upgrades.
In both cases, the files cannot be decrypted by either the World Foundation or Tools for Humanity. The system has been designed to intentionally keep your data secure even in the case of a potentially malicious actor.
Why is Personal Custody important?
Personal Custody is a key example of user-centric architecture, which is an important part of the World Tech Tree.
When system architecture is focused around you, the user, it’s easier to separate and replace other system components like “Orbs” and “uniqueness”—separation that’s necessary to build an open, permissionless protocol that can be owned and governed by the largest number of people possible (learn more about this here).
Additionally, with Personal Custody, optional Data Custody will no longer be offered at the time of your Orb visit. This helps ensure everyone can learn about World before deciding if they’d like to share their information to help improve the project.
Learn more
For more information on the Orb, privacy and the World Tech Tree, see the Technical Implementation section of the World protocol whitepaper.
You can also learn more about the World protocol by visiting the World website, joining the daily conversations on Twitter/X, Telegram, Discord, YouTube and LinkedIn, or signing up for the blog newsletter at the bottom of this page.
Haftungsausschluss
The above content speaks only as of the date indicated. Further, it is subject to risks, uncertainties and assumptions, and so may be incorrect and may change without notice. A full disclaimer can be found in our Terms of Use and Important User Information can be found on our Risks page.